Demoing your website
How to expose your local web server to the internet without public IP or router changes
Once in a while there is a need to share your work-in-progress website, built on technologies like NextJS, Nuxt, hugo or any other framework, tool, etc..
Sometimes it is way too early in the development cycle to set up automated (or not) deployment just to get some feedback; this is where tunnels come in. In this example we will run a local NextJS server. I will create an example app with:
npx create-next-app@latest \
nextjs-blog \
--use-npm \
--example "https://github.com/vercel/next-learn/tree/main/basics/learn-starter"
and start it
cd nextjs-blog
npm run dev
I can view it on http://localhost:3000:
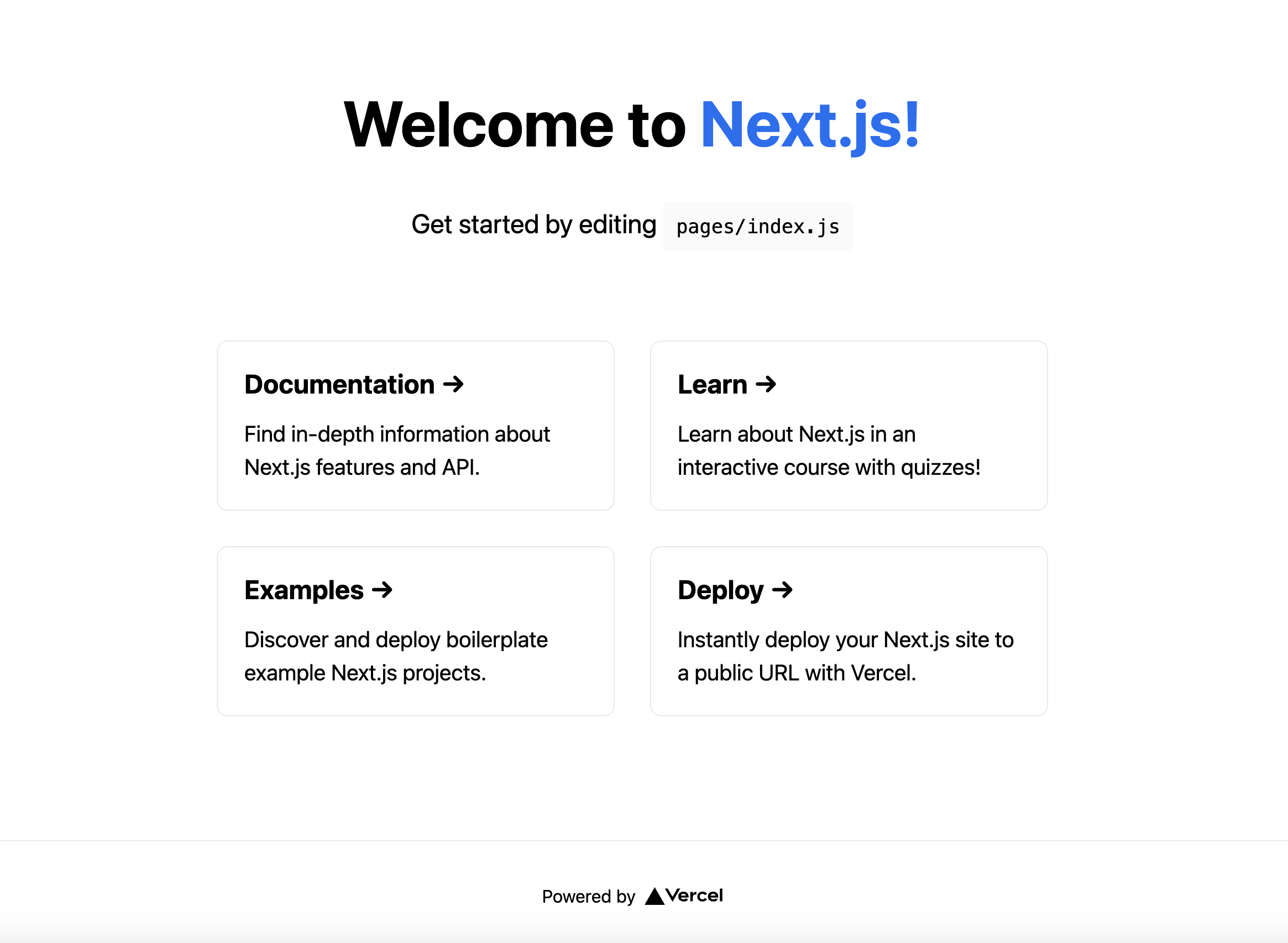
This is running on my local machine, and I want to share it with my friends. Now, to expose it to the internet, I can use the following command:
relay connect --name my-tunnel http://localhost:3000
These commands have to be run in two separate terminal windows:
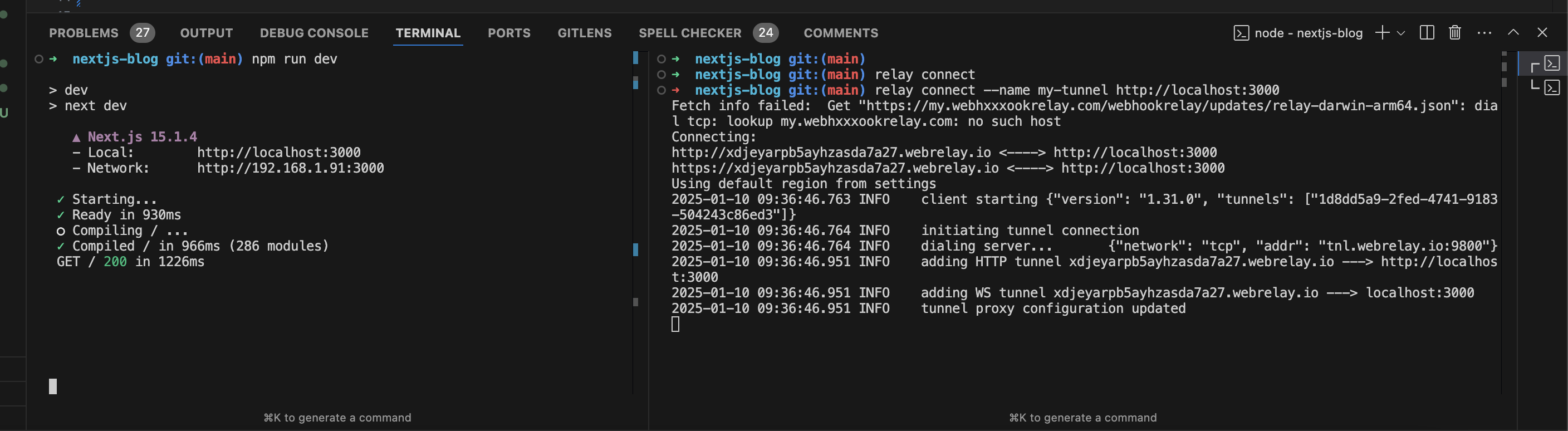
Click on the link in the terminal to open the browser and view the website:
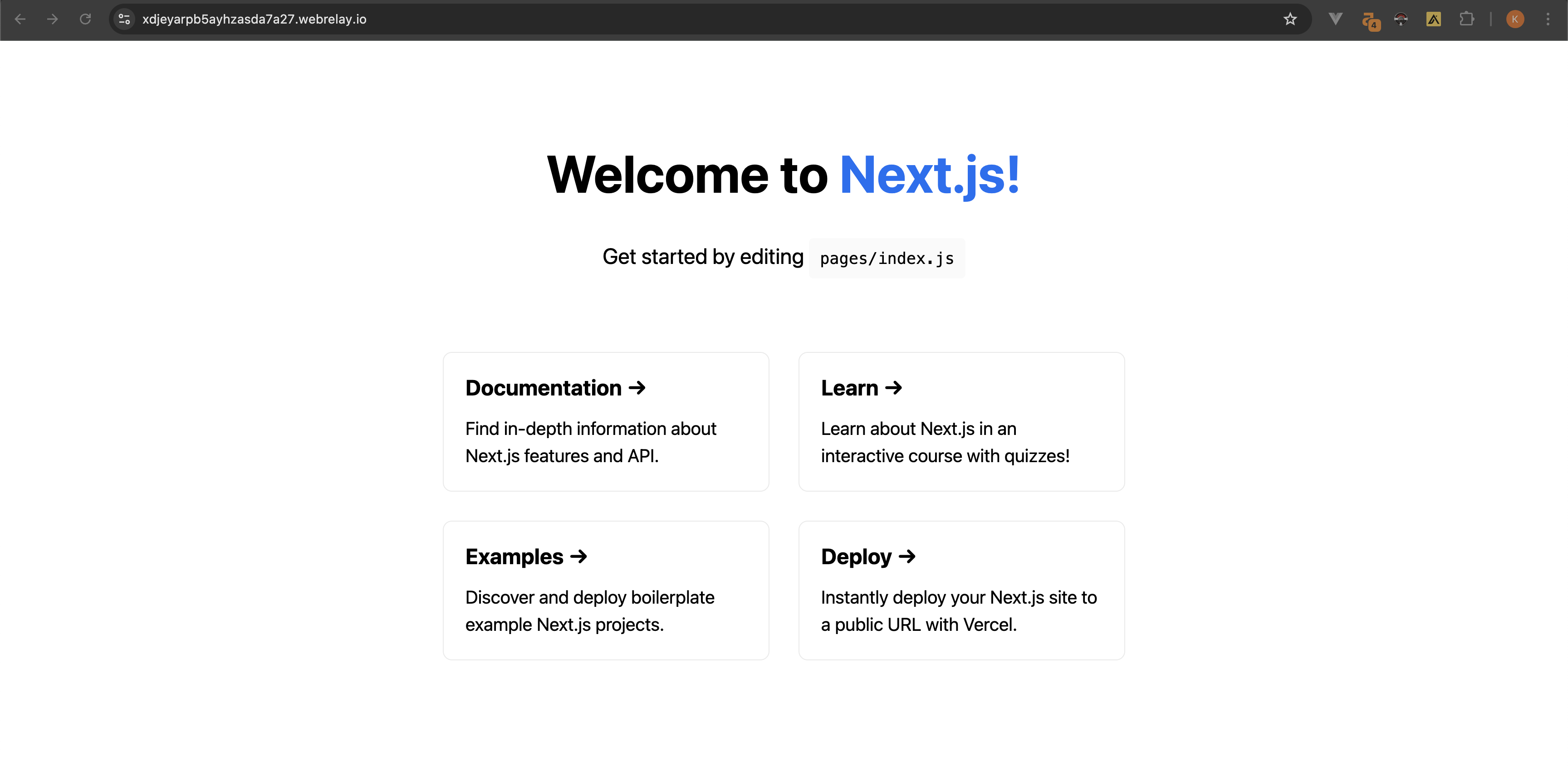
That's it!

