Home Assistant
Connecting to your Home Assistant remotely without domain/public IP or configuring NAT.
How does it work?
Webhook Relay for home automation addons work exactly the same as our CLI or webhookrelayd tunneling daemon. These local agents create a reverse tunnel back to the https://my.webhookrelay.com cloud service. Any HTTP requests received by the public endpoints will be routed to your private endpoints. Webhook Relay provides end-to-end encryption, both tunnel and public endpoints use HTTPS for webhook forwarding. If you are using tunnels, HTTPS is optional (defaults to enabled) for all paid plans.
What's the use case?
Webhook Relay addon helps to receive webhooks by popular services such as IFTTT or Zapier and relay them to your Home Assistant or Node-RED instances. It can also be used for remote access if you are using tunnels. Since webhooks are just a standard HTTP requests, any services can easily produce and consume them. Webhook Relay is particularly useful when:
- You cannot access your router to configure port forwarding
- Router doesn't support port forwarding
- Your ISP blocks inbound connections
- You don't have a static IP address
- Server that is hosting your home automation system is changing IP, location
You should use webhooks forwarding when:
- Service that is sending requests to your home automation instance doesn't expect responses (usually webhook producers don't expect anything)
- Additional security is required for your server and you don't want to expose it to the internet. Webhooks producer won't get any information about the server that is consuming your webhooks
You should use tunnels when:
- You need remote access to your home automation instance (for example you want to view it through the browser).
- Service that is calling your home automation instance wants to receive responses from it.
Security best practices
Like with any technology, some knowledge about Webhook Relay offered features is required. First of all, applications usually set cookies or JWT tokens. It is important to keep this information secure and you should not use HTTP (non-HTTPS) tunnels for this. Make sure:
- You use TLS pass-through tunnels with your own certificates (add-on can generate Let's Encrypt certificates for DuckDNS or generate self-signed ones).
- You expose only those services that need to be exposed. Use webhook forwarding functionality when the server doesn't have to respond (for example you are receiving webhooks and don't need remote access via your browser).
Home Assistant
Webhook Relay provides a secure, stripped down tunneling daemon webhookrelayd which can be used as a Home Assistant add-on.
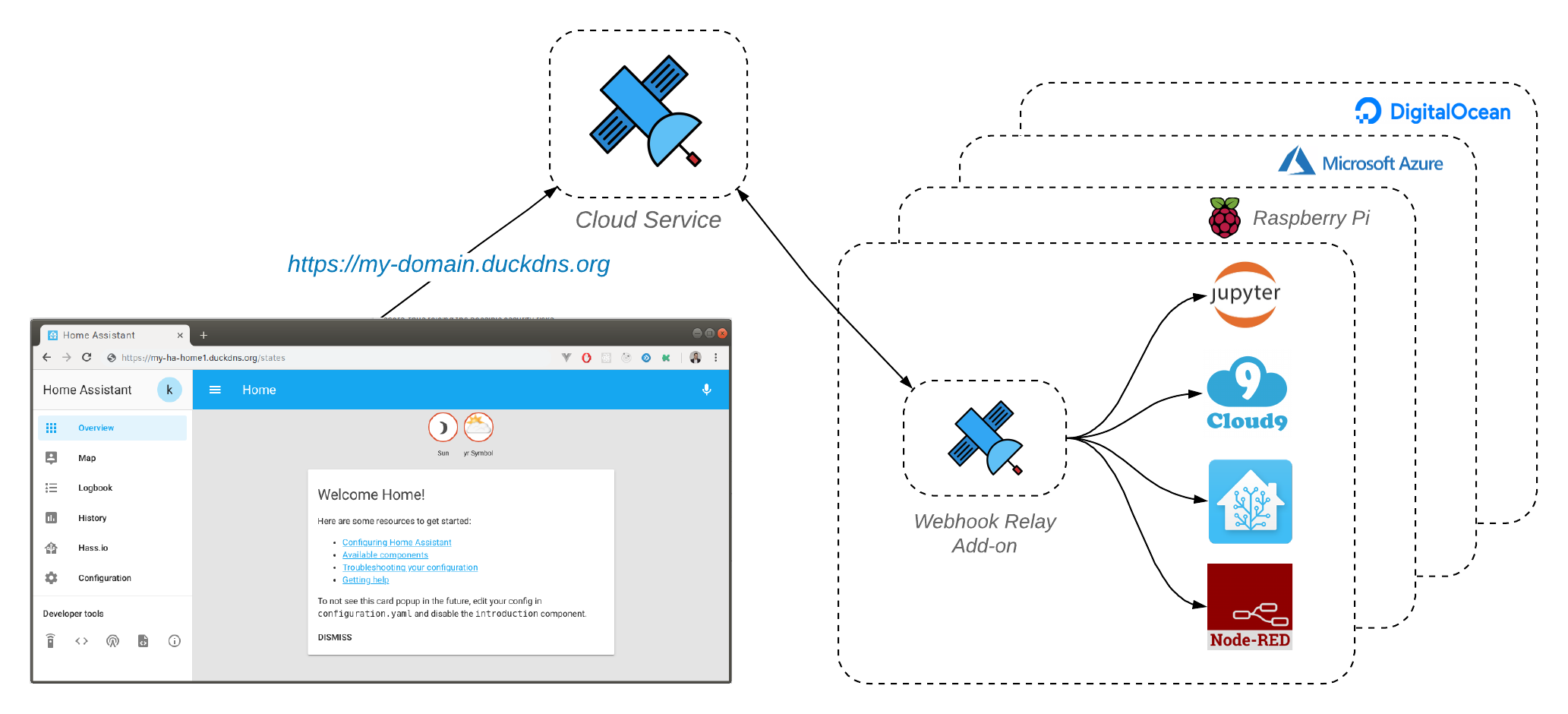
Installation
There are several configuration options for this add-on. You can always mix and match them (Simple HTTPS, DuckDNS, Cloudflare).
Installation instructions can be found here. Most popular configuration uses DuckDNS as it provides you with your own free subdomain that can be used to retrieve TLS certificates.
Cloudflare integration
If you have your own domain name, you can follow instructions in the Cloudflare section to start using it.
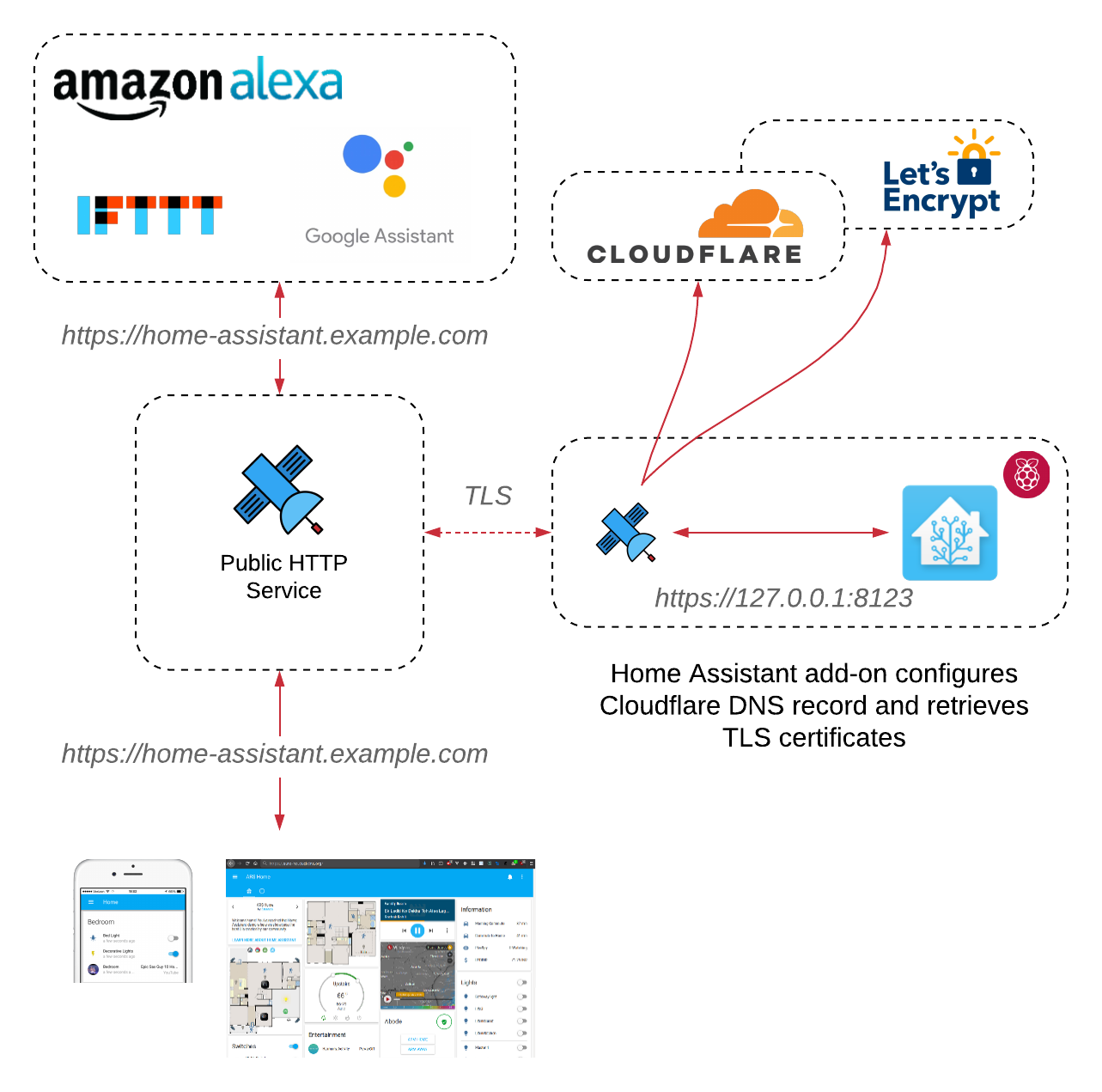
On top of it allowing you to have any domain names with TLS pass-through tunnels, you get some additional benefits:
- Minification - Remove unwanted characters like whitespaces, comments, new line characters, block delimiters which are not needed for a web page to serve.
- Cloud WAF - WAF (Web Application Firewall) help to keep your site secure from OWASP top 10, CMS (WordPress, Joomla, etc. ) vulnerabilities. Cloudflare WAF got more than 145 rules to protect from almost all types of web applications attack.
- Browser Caching
- Optimized Network Routing
Issue reporting & support
If you have any questions or have encountered an issue. Please check Webhook Relay addon logs and supply them here https://github.com/webhookrelay/home-assistant/issues or email us at [email protected]
FAQ
Q: Does using Webhook Relay to forward webhooks makes my Home Assistant instance less secure?
A: Using our service makes your Home Assistant more secure, as webhook forwarding is one-way traffic only and no information about your Home Assistant can be retrieved.
Q: Is free plan enough for me?
A: Depends on your usage. If you just want to relay webhooks to your internal Home Assistant server then using free tier should be enough, current limit is 150 webhooks per month. If you want to access it remotely via tunnels, we would recommend to subscribe to a basic plan which is just 4.5$ per month and get secure HTTPS tunnels.
Q: Why are webhooks recorded?
A: Webhook Relay is used by engineers and developers to develop, debug and proxy various webhook requests to other services. Recording enables you to inspect the traffic. Only you or your sub-accounts can access them. Usually webhooks don't store any sensitive information.
Q: Is tunnel traffic recorded?
A: No, you can view our GDPR policy. Tunnel traffic is not recorded. Also, please use TLS tunnels whenever possible for maximum protection.
Q: Do phone push notifications work with the tunnels?
A: Push notifications are based on HTTP2 standard that requires TLS all the way. It will work if Home Assistant has TLS enabled (you would be accessing it locally over https://192.168.*.*:8123). To do that, you can generate certificates yourself and just supply in the tunnel to not do TLS termination. Example configuration:
{
"key": "[YOUR TOKEN KEY]",
"secret": "[YOUR TOKEN SECRET]",
"forwarding": [],
"tunnels": [
{
"name": "home-assistant",
"destination": "https://127.0.0.1:8123",
"protocol": "tls",
"subdomain": "[YOUR SUBDOMAIN]",
}
],
"cloudflare": {
"email": "",
"api_key": ""
},
"duck_dns": {
"token": "",
"accept_terms": false
},
"tunnels_enabled": true,
"forwarding_enabled": false
}

